firmware
Now that we’re fresh into the start of 2026, I thought it would be interesting to take a look back at the state of automotive cybersecurity. To do this, I wanted to answer the question of: What is the state of automotive vulnerability reporting in 2026?
Another day, another teardown - and the first blog post of 2026! Today we’ll be looking at the BMW IDC23H infotainment unit, manufactured by Harman Becker.
The IDC23H is one of the newest infotainment units from BMW, as of January 2026. The design is based on the previous-generation MGU22/MGU22H, and is used in a wide variety of BMW models - this unit in particular was found in one of BMW’s newest X1 U11 SUVs.
For the past 2-or-so years, I’ve been hacking on my car’s infotainment unit - the BMW NBT EVO HU. I figured this would be the perfect opportunity to dive into a new topic: What does the boot process of a modern QNX-based infotainment unit look like?
Today’s teardown is of the BMW NBT EVO HU, an infotainment unit built by Harman Automotive - sound familiar?
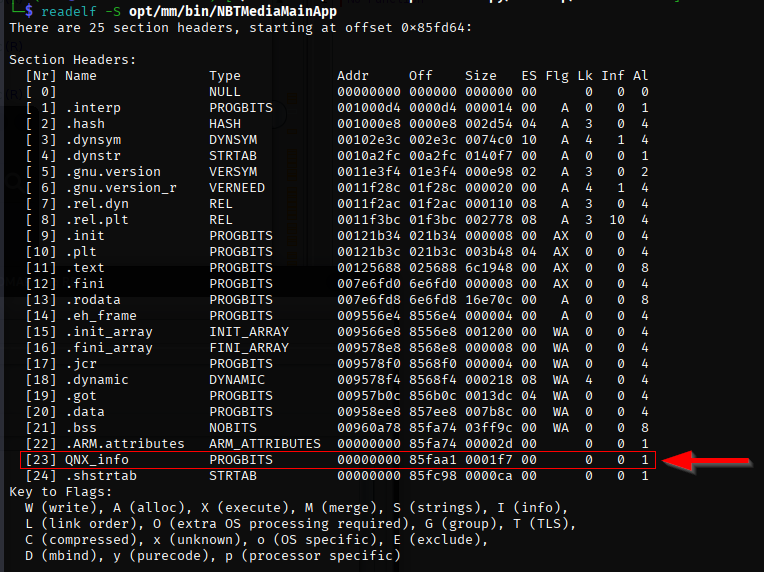
When poking at binaries on a QNX-based system, you may run into an interesting ELF header: The so-called QNX_info section!
Today’s teardown is of the BMW NBT HU infotainment unit, built by Harman Automotive. This head unit was used between 2012 and 2019 across a wide array of models in BMW’s lineup, in everything from their sedans to SUVs.
The goal was simple: For the past year or so, I’ve been poking at my car’s head unit in my free time. This has now escalated to the point where I have two or three of the head units…
They use a 1mm-pitch edge connector for debugging and development access, and I didn’t want to solder wires directly to the pins in an irreversible way. As such, I created a breakout board!
It’s not often you look to extract an embedded device’s firmware over the network. Luckily, it’s possible with SSH! We’ll go over a few techniques for dumping raw block device bytes out onto the network to facilitate quick extraction of device firmware for static analysis on a separate host computer.
The device I’m currently working with has over five hundred shared libraries, all spread out across random folders within the filesystem. Bleh!
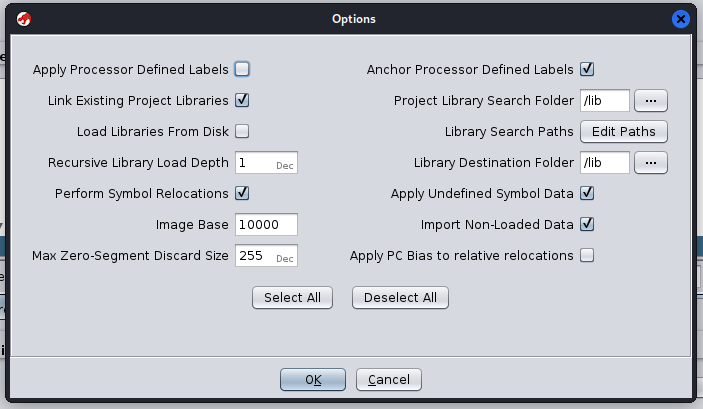
This is a common issue I’ve run into when working with embedded systems. You want to import an arbitrary binary into Ghidra, but first you have to spend 10 minutes tracking down where all of it’s shared libraries are located! A major pain.
But have no fear, a one-liner is here! (every Linux graybeard’s favorite saying)
In general, most software security operates on the basis of sources and sinks - vulnerable data, input, influence, etc. comes from a known source, and eventually reaches a vulnerable sink. When thinking of a single binary, this concept can be fairly straightforward:
If a binary takes input via argv that eventually ends up in a system() call and leads to command execution, argv() is the source, and system() is the sink.
But what about when thinking of an entire embedded system, rather than just a single binary?
This is where the concept of border binaries come into play!
In the beginning of December, I published a new tool I wrote for analyzing ELF files! This tool is aimed at helping reverse engineers and tinkerers understand embedded filesystems quickly and easily, through ergonomic methods of displaying in-depth device and binary metadata.
Here’s your five second tip of the day: Need to install CaringCaribou on a system you don’t have root on? (For example: a CTF VM)




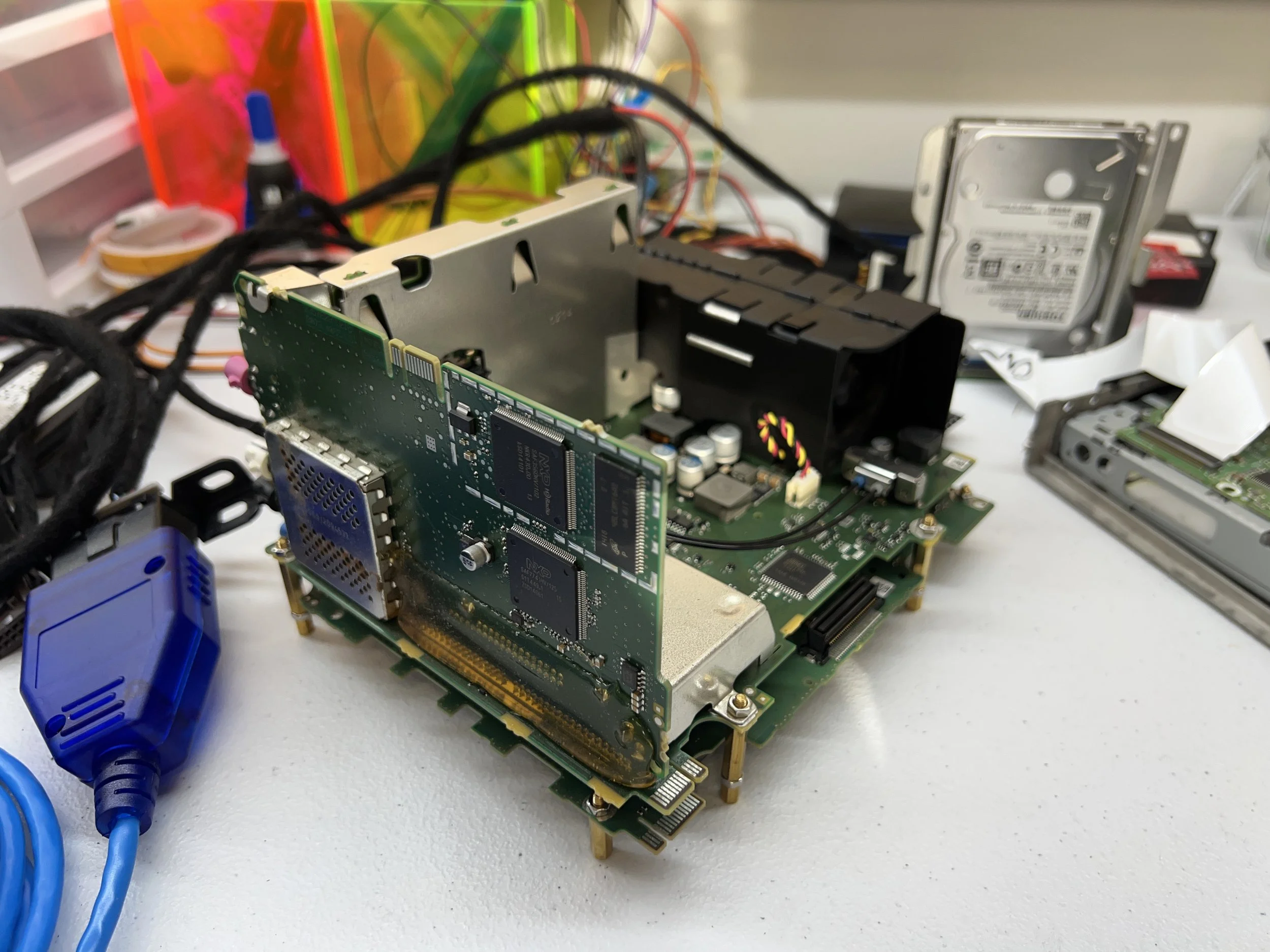
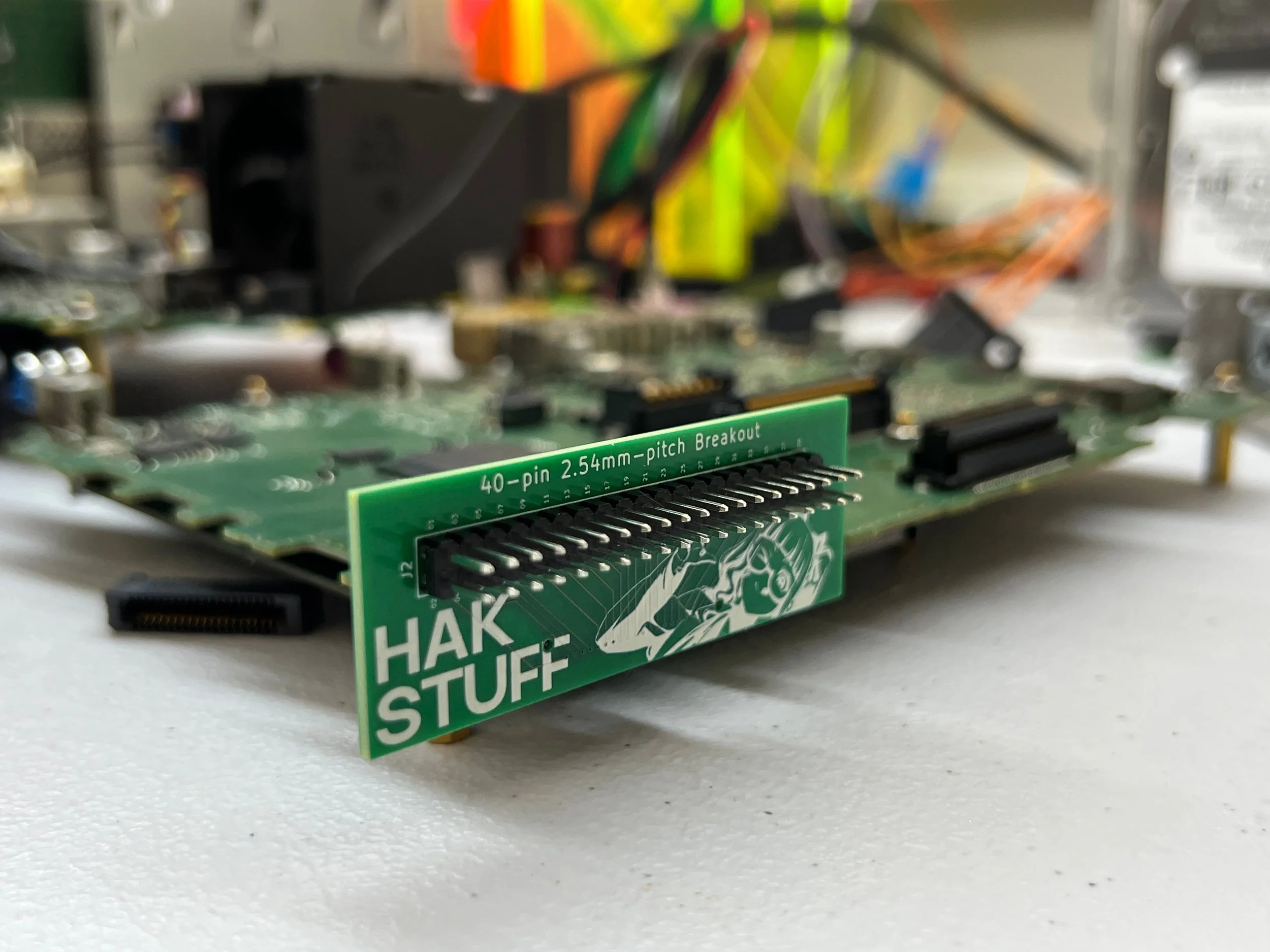




There isn’t a lot of content online discussing how to dump a QNX IFS partition, so I thought I’d write up a few paragraphs here to spread the tips and tricks that I’ve learned.
(If you just want the tl;dr and already know what IFS partitions are, scroll to the bottom!)